//Kevin Anderson /May 2 / 2013
How to keep your editorial Twitter accounts from being hacked
Major news organisations including Reuters, Al Jazeera, CBS, NPR, the BBC, The Guardian and the Associated Press have all made headlines in the past year after hackers took over their Twitter accounts. The attacks are always embarrassing and can negatively impact the reputation of your news organisation, but the attacks can also cause panic and real damage, as we saw recently.
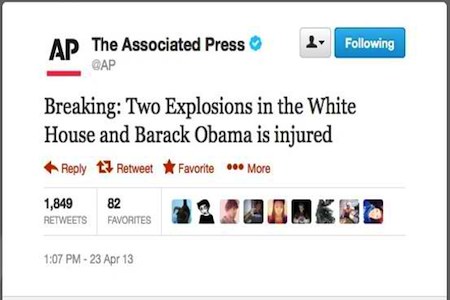
The fake tweet posted to the AP Twitter account said:
Breaking: Two Explosions in the White House and Barack Obama is injured.
Literally, within a minute after the fake tweet was posted, the Dow Jones Industrial Average dropped 150 points. Bloomberg reported that the attack wiped out $136 bn of market value from the Standard & Poor’s 500 stock index. Within three minutes of the tweet being posted, AP journalists were posting on their own accounts that the tweet was a hoax and that the news organisation had been hacked.
While major international English and Arabic news organisations have been targets, the same tactics are being used by politically motivated hackers everywhere. In the lead up to the general election in Malaysia, the Twitter accounts of the independent news website Malaysiakini were hacked and taken control of by a group calling itself Sarkas-Siber. (For transparency, Media Development Investment Fund, which publishes Knowledge Bridge, has provided debt and equity financing and strategic advice to Malaysiakini.)
Twitter warned news organistions that the attacks will continue, and that journalists and news groups will “continue to be high value targets to hackers”. The microbloggingMicrobloggingPublishing very brief, spontaneous posts to a public Website, usually via a…//read more platform is working on tightening security on its platform, but as it does, it offered up a number of recommendations for news groups to keep their accounts secure.
Victims of ‘spear phishing’
Like most hacks, most of these attacks against the BBC, The Guardian and the Associated Press weren’t technically sophisticated. Contrary to the movie stereotype of elite hackers defeating advanced computer security, the attacks didn’t rely on technical wizardry but rather on social engineering, which is just a fancy computer security term for scamming users out of username and password information. All three news organisations were targeted and successfully compromised by the Syrian Electronic Army (SEA), a group that supports Syrian President Bashar al-Assad and accuses western news organisations of spreading “lies and slander about Syria“.
All three news organisations say that they were the target of phishing attacks. Most people know phishing from the suspicious emails that appear from scammers trying to trick you out of your credit card and bank details. These attacks, often known as spear phishing due to their targeted nature, are much more targeted, more personalised and much harder to spot as frauds than the standard email fraud schemes. James Ball, the data editor at the Guardian, wrote on Twitter:
The guys doing the Guardian phishing attack I mentioned yesterday (it’s SEA) are really very good: sustained, changing, mails today.
He mentioned earlier that the emails were specifically targeting Guardian journalists. As one of the commenters says on a Naked Security blog post discussing the attack, “spoofing” an email – faking the sender’s email address – is trivial for most hackers. Both the AP and the BBC reported phishing attacks around the time that their Twitter accounts were compromised. According to the USA Today newspaper, the BBC warned staff about the suspicious emails:
The BBC’s email to staff said the “phishing” emails contained what appeared to be links to The Guardian newspaper or Human Rights Watch online and bring users to a fake webmail portal.
Twitter scrambles to respond
Twitter made a number of recommendations to news organisations to help them protect themselves. Some of the the tips are sensible online security such as changing passwords on a regular basis and having strong passwords. Twitter suggested that the passwords should be 20 characters long and a mix of characters and numbers or random words. Most security experts advise against using words that appear the dictionary, although a mix of random words would be more difficult to crack.
Other advice that Twitter offered news groups is impractical. They suggested that news organisations should have a dedicated computer to post to Twitter that they didn’t use to access email or the web.
Twitter did reachReach1) unique users that visited the site over the course of the reporting period,…//read more out to news organisations asking that they work more closely with the company. Twitter wrote in a memo to news groups:
Help us protect you. We’re working to make sure we have the most updated information on our partners’ accounts.
The advice is not just coming from Twitter but is also being given to Twitter to step up its own security. Specifically, a number of security experts have encouraged the company to adopt two-step authentication, something that Google rolled out after high-profile hacking attacks that were revealed in 2010. Two-step authentication often requires a user to register a mobile phone so that codes can be sent as a second step to log into an account on a new computer or device. Facebook, Google and Yahoo! all use the added security feature.
Protecting yourself against spear phishing
However, the best line of defence begins by educating all editors, managers and staff on security best practices. Hackers and phishers are always developing new ways to trick you into compromising your own security, and as Twitter says, journalists are now targets not only for politically motivated hacktivists but also by unfriendly governments.
We’ve all become more aware of scammers trying to trick us out of our credit card or bank details. We all know to take care when opening attachments or clicking on links in emails from people we don’t know. But it is important to understand the new and evolving techniques that spear phishers use to trick you into giving up your usernames, passwords and other important details. As the experts at Norton Security say:
The spear phisher thrives on familiarity. He knows your name, your email address, and at least a little about you.
As journalists we live in public, and it will be all that much easier for hackers to build up a profile to target us. Moreover, as Norton notes, spear phishers are stalking you on social networks. Think of all of the information that you post on social networks and how easy it would be for an attacker to dupe you into believing that they are a friend. Norton asks:
How safe you and your information remain depends in part on you being careful. Take a look at your online presence. How much information is out there about you that could be pieced together to scam you? Your name? Email address? Friends’ names? Their email addresses?
Norton recommends that if you receive an email from a friend asking you for a password or other sensitive information that you call them up to verify the email is from them.
As journalists, we’re trained to be sceptical, and it’s important to use that skill to bolster your electronic security. Be wary of emails purportedly from friends or organisations you know asking for or directing you to sites asking you for business sensitive information. That moment of caution could prevent your Twitter account from being compromised, your contacts from being stolen or your news organisation’s office network from being breached.
Article by Kevin Anderson

Leave your comment